TLS/SSL Server Elliptic Curve Support
Abstract
With APAR PI99184, the z/VM TLS/SSL Server Elliptic Curve Cryptography support enables new cryptographic algorithms that were added for use by System SSL V2.1. Elliptic Curve Support is, due to the mathematical nature of its processing, considered to be a faster and more secure mechanism for asymmetric encryption than the standard RSA or DSS algorithms. One workload was used to evaluate the changes. Using a Telnet connection ramp-up workload, as the number of existing connections increased to 600, on average the SSL server CPU/tx decreased by 77% with an Elliptic Curve (EC) cipher when compared back to a non-EC cipher.
Method
A Telnet-connect workload was used to evaluate the new EC cipher support.
Figure 1 describes the Telnet-connect workload setup.
| Figure 1. 600 Secure Telnet Logo Connections. |
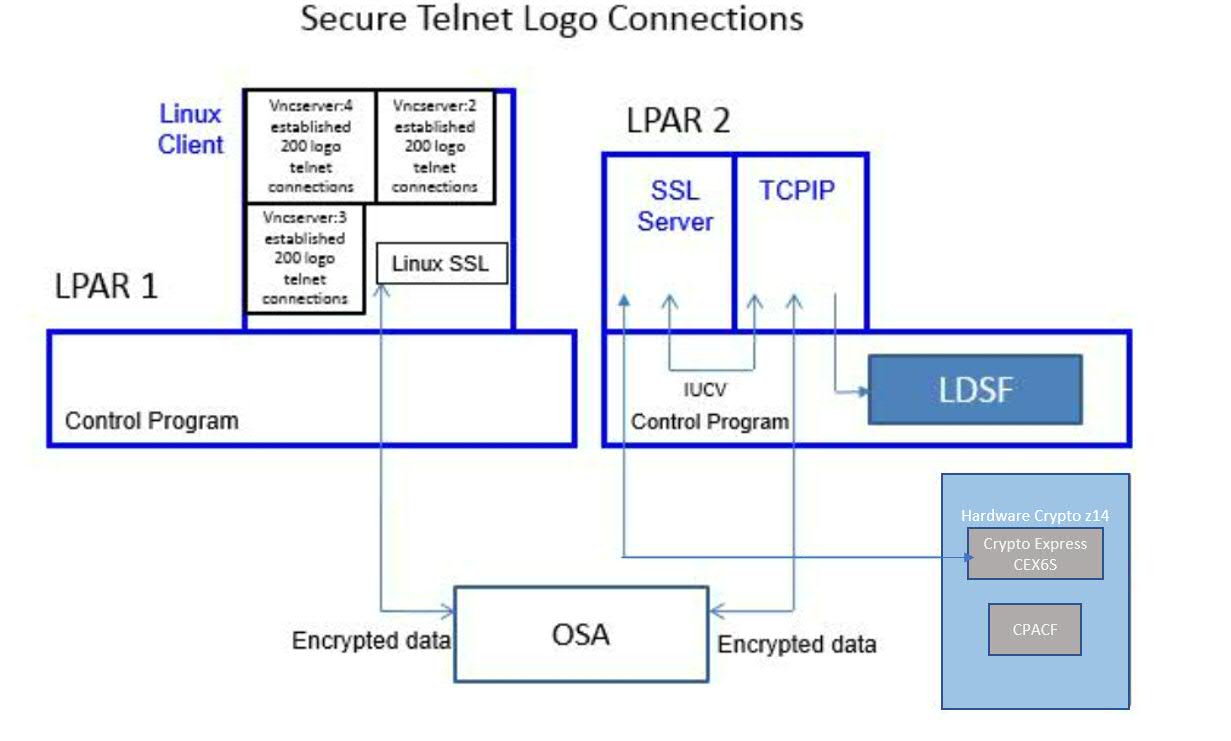
|
| Notes: CEC model 3906-M05, Crypto Express CEX6S, CP Assist for Cryptographic Function (CPACF) Support, z/VM 7.1 |
A Linux client driving the workload was running on LPAR 1. The Linux client opened a total of three VNC servers. Each VNC server established 200 Telnet connections to LPAR 2. The CMS-based SSL server was running on LPAR 2. The two LPARs communicated via OSA.
IBM collected MONWRITE data during measurement steady state and reduced with Performance Toolkit for VM. A transaction was one successful Telnet connection. The workload throughput was controlled by the Linux client initiating one Telnet connection every half a second. The TCPU column in FCX162 USERLOG for the SSL server was used to calculate guest CPU per transaction.
Results and Discussion
Telnet Connection
Table 1 shows the CPU time to establish a new Telnet connection versus existing number of connections.
| Table 1. CPU Milliseconds Needed for a New Connection | ||||
| Existing | Non-EC | EC | Delta | %Delta |
| 0-60 | 45.41 | 7.11 | -38.30 | -84.3 |
| 60-120 | 45.65 | 8.73 | -36.92 | -80.8 |
| 120-180 | 49.05 | 9.85 | -39.20 | -79.9 |
| 180-240 | 50.43 | 10.58 | -39.85 | -79.0 |
| 240-300 | 49.16 | 12.36 | -36.80 | -74.8 |
| 300-360 | 53.11 | 13.38 | -39.73 | -74.8 |
| 360-420 | 57.63 | 13.75 | -43.88 | -76.1 |
| 420-480 | 58.93 | 16.65 | -42.28 | -71.7 |
| Mean | -77.7 | |||
| Notes: CEC model 3906-M05, Crypto Express CEX6S, CP Assist for Cryptographic Function (CPACF) Support, non-EC cipher: DHE_RSA_AES_128_SHA256, EC cipher: ECDHE_RSA_AES_128_SHA256 | ||||
Chart 1 shows a graph of the same information.
| Chart 1. SSL CPU Time to Establish a New Connection versus Existing Connections. |
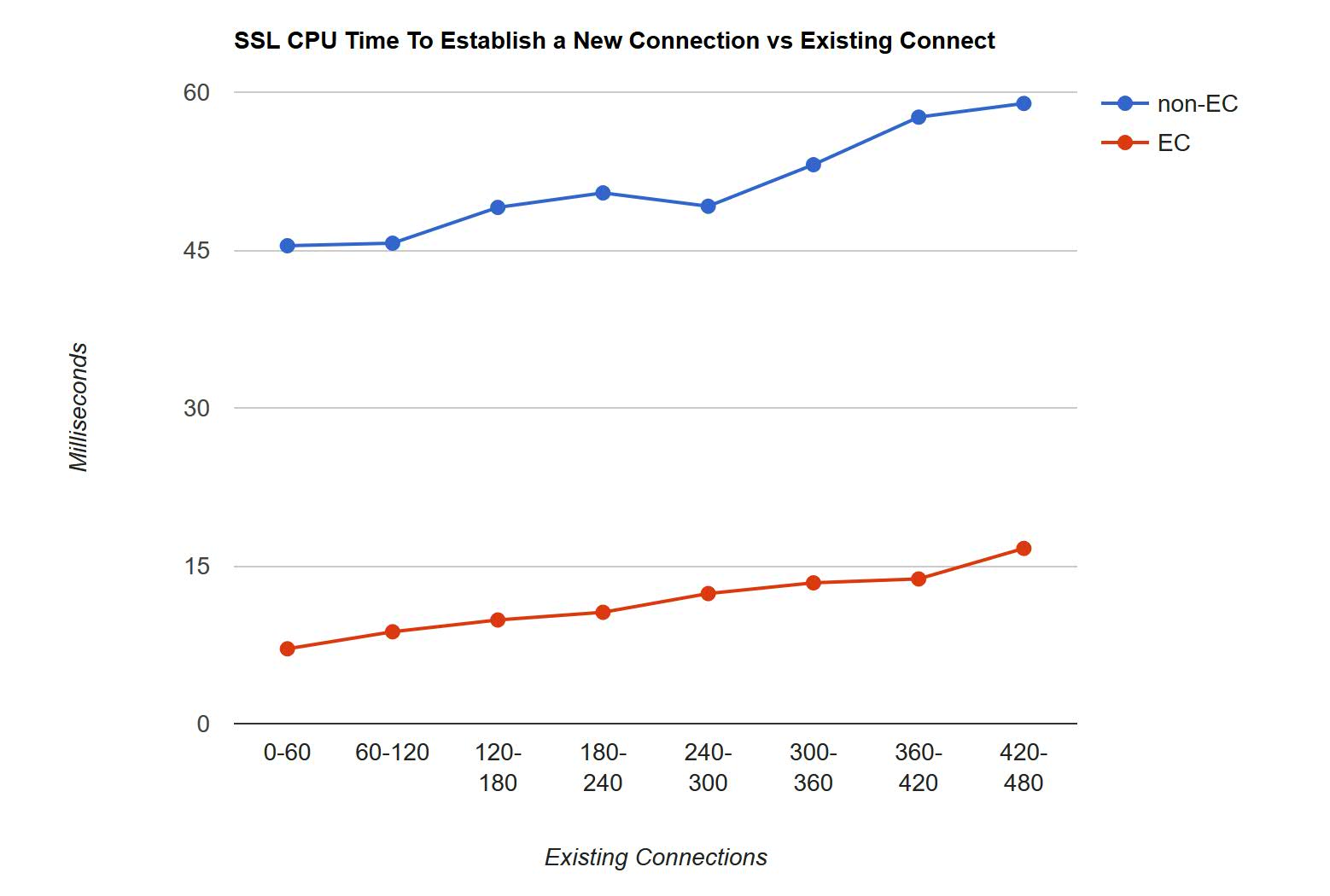
|
|
Notes:
CEC model 3906-M05,
Crypto Express CEX6S,
CP Assist for Cryptographic Function (CPACF) Support,
non-EC cipher: DHE_RSA_AES_128_SHA256, EC cipher: ECDHE_RSA_AES_128_SHA256 |
With both the non-EC cipher and EC cipher, the CPU time to establish a connection gradually increased with existing number of connections for the SSL server. On average, over the measurement period, the SSL server CPU time to establish a new connection decreased by 77% with an EC cipher.
Summary
With EC, the average SSL CPU time to establish a new Telnet connection decreased by 77% when compared back to an equivalent non-EC cipher.