RSCS TCPNJE Encryption
Abstract
Secure TCPNJE links for RSCS was introduced in z/VM 6.3 with the PTF for APAR VM65788. When compared to a non-secure RSCS link, transferring files across z/VM 6.3 LPARs over an RSCS link secured by TLS 1.0 and RSA_AES_256 resulted in total CPU/tx increasing by 56% for the SSL server, TCPIP, and RSCS combined.
Transferring files across z/VM LPARs in a z/VM 6.3 - TLS 1.2 - RSA_AES_128_SHA256 environment resulted in total CPU/tx decreasing by 2.1% for the SSL server when compared back to a z/VM 6.3 - TLS 1.0 - RSA_AES_256 environment.
With z/VM 6.4 the SSL default TLS protocol was increased from TLS 1.0 to TLS 1.2, the default cipher strength increased from RSA_AES_256 to RSA_AES_128_SHA256, and the System SSL level upgraded from V2.1 to V2.2. A z/VM 6.3 environment using the TLS 1.2, RSA_AES_128_SHA256 and System SSL level V2.1 experienced a slight increase in CPU/tx when upgrading to a z/VM 6.4 environment. The SSL server CPU/tx increased 6.3%.
Introduction
Encryption of TCPNJE connections was introduced in z/VM 6.3 with the PTF for APAR VM65788 which enables encrypted TCPNJE traffic over RSCS. A new TCPNJE-type link parameter called TLSLABEL has been added. This parameter specifies the label of a digital certificate that will be used to encrypt/decrypt all data flowing over the link. The same certificate label must be specified on both sides of the link. The specified certificate and its corresponding TLSLABEL must exist in the TLS/SSL server certificate database. For additional information on the TLS/SSL server and managing its certificate database refer to z/VM TCP/IP Planning and Customization.
Method
One workload was used to evaluate the CPU cost of encrypting/decypting data flowing over a secure RSCS TCPNJE link. Figure 1 shows how two LPARs were defined with a RSCS TCPNJE link. Two files were sent back and forth between USER1 located on LPAR 1 and USER2 located on LPAR 2 over the RSCS TCPNJE link. One file was a large CMS file with 1 million records and a F1024 LRECL. The second file was a small CMS file with 20 records and a F1024 LRECL. The RSCS REROUTE command was used to cause the files to bounce back and forth during the measurement. The RSCS REROUTE command instructs RSCS to reroute the files automatically once received.
When the link was started without the TLSLABEL parameter data flow did not include the SSL server. When the link was started with the TLSLABEL parameter data flowed to the SSL server for encryption/decryption processing.
The two LPARs communicated via OSA.
| Figure 1. Encryption of TCPNJE connections. |
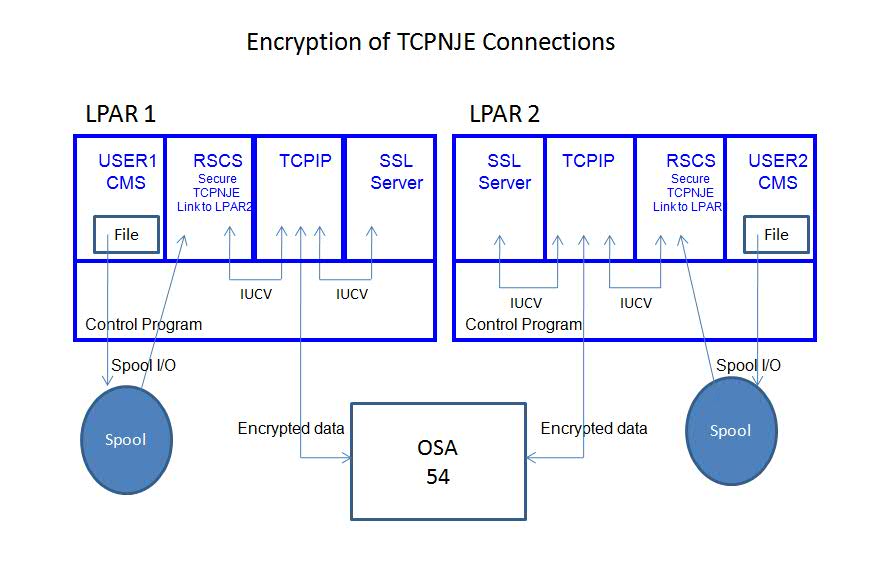
|
| Notes: Processor 2827-HA1, CP Assist for Cryptographic Function (CPACF) |
Table 1 contains configuration parameters for the four environments measured.
| Table 1. Configurations measured. | |||||
| Case Number | Security | z/VM Level | SSL Version | TLS Protocol | Cipher |
| case 1. | not secured | z/VM 6.3 with the PTF for APAR VM65788 | SSL V2.1 | na | na |
| case 2A. | secured | z/VM 6.3 with the PTF for APAR VM65788 | SSL V2.1 | TLS 1.0 | RSA_AES_256 |
| case 2B. | secured | z/VM 6.3 with the PTF for APAR VM65788 | SSL V2.1 | TLS 1.2 | RSA_AES_128_SHA256 |
| case 3. | secured | z/VM 6.4 | SSL V2.2 | TLS 1.2 | RSA_AES_128_SHA256 |
|
Notes:
CEC model 2827-HA1;
CP Assist for Cryptographic Function (CPACF) support: Yes
| |||||
For all measurements IBM used a 2827-HA1 processor and its CP Assist for Cryptographic Function (CPACF) facility. It should be noted the system configuration was designed to have no CPU constraints or memory constraints.
IBM collected MONWRITE data during measurement steady state and reduced it with Performance Toolkit for VM. External throughput (ETR) was calculated by summing the FCX215 FCHANNEL Write/s and Read/s columns for chpid 54 and then dividing by a scaling constant. Guest CPU utilization came from dividing the FCX112 USER TCPU value by the duration of the MONWRITE file in seconds. CPU time per transaction was then calculated by dividing CPU utilization by ETR. This was done for the SSL, TCPIP, and RSCS servers.
Results and Discussion
Table 2 shows a comparison of case 2A back to case 1. This illustrates the effect of adding basic encryption to a z/VM configuration.
| Table 2. Secure TCPNJE link vs. non-secure TCPNJE link. | ||||
| Non-Secure TCPNJE Link | Secure TCPNJE Link | Delta | Percent Difference (%) | |
| Runid | TCPX108D | TCPX1081 | ||
| ETR | 267 | 257 | -10.00 | -3.7 |
| SSL server CPU/tx | 0.000 | 0.047 | 0.047 | na |
| TCPIP server CPU/tx | 0.011 | 0.035 | 0.024 | 218.2 |
| RSCS server CPU/tx | 0.154 | 0.175 | 0.021 | 13.6 |
| Servers combined CPU/tx | 0.165 | 0.257 | 0.092 | 55.7 |
|
Notes:
CEC model 2827-HA1;
z/VM 6.3 with the PTF for APAR VM65788; TLS Protocol 1.0;
Cipher Strength RSA_AES_256.
| ||||
With a secure link the SSL server consumed 0.047 CPU/tx. The TCPIP server CPU/tx increased by 218.2%. The RSCS server CPU/tx increased by 13.6%.
Table 3 shows a comparison of case 2B back to case 2A. This illustrates the effect of increasing the encryption strength default.
| Table 3. Secure TCPNJE link with TLS 1.2 - RSA_AES_128_SHA256 vs. secure TCPNJE link with TLS 1.0 - RSA_AES_256. | ||||
| Secure Link with TLS 1.0 | Secure Link with TLS 1.2 | Delta | Percent Difference (%) | |
| Runid | TCPX1081 | TCPX108C | ||
| ETR | 257 | 270 | 13.00 | 5.1 |
| SSL server CPU/tx | 0.047 | 0.048 | 0.001 | 2.1 |
| TCPIP server CPU/tx | 0.035 | 0.033 | -0.002 | -5.7 |
| RSCS server CPU/tx | 0.175 | 0.148 | -0.027 | -15.4 |
| Servers combined CPU/tx | 0.257 | 0.229 | -0.028 | -10.9 |
|
Notes:
CEC model 2827-HA1;
z/VM 6.3 with the PTF for APAR VM65788.
| ||||
The SSL server CPU/tx increased by 2.1% with the higher TLS protocol and cipher strength. The CPU/tx for the TCPIP and RSCS servers decreased by 5.7% and 15.4% respectively.
Table 4 shows a comparison of case 3 back to case 2B. This illustrates the effect of moving from z/VM 6.3 to z/VM 6.4 while keeping the cipher strength constant.
| Table 4. Secure TCPNJE link z/VM 6.4 vs. secure TCPNJE link z/VM 6.3. | ||||
| Secure Link with z/VM 6.3 with the PTF for APAR VM65788 | Secure Link with z/VM 6.4 | Delta | Percent Difference (%) | |
| Runid | TCPX108C | TCPY722M | ||
| ETR | 270 | 332 | 62.00 | 23.0 |
| SSL server CPU/tx | 0.048 | 0.051 | 0.003 | 6.3 |
| TCPIP server CPU/tx | 0.033 | 0.036 | 0.003 | 9.1 |
| RSCS server CPU/tx | 0.148 | 0.166 | 0.018 | 12.2 |
| Servers combined CPU/tx | 0.229 | 0.253 | 0.024 | 10.5 |
|
Notes:
CEC model 2827-HA1;
TLS Protocol 1.2 - RSA_AES_128_SHA256.
| ||||
The SSL server CPU/tx increased by 6.3% in the z/VM 6.4 environment. The CPU/tx for the TCPIP and RSCS servers increased by 9.1% and 12.2% respectively.
Summary and Conclusions
Transferring files across z/VM 6.3 LPARs over an RSCS link secured by TLS 1.0 and RSA_AES_256 resulted in total CPU/tx increasing by 56% for the SSL server, TCPIP, and RSCS combined when compared back to a non-secure RSCS link.
Transferring files across z/VM LPARs in a z/VM 6.3 - TLS 1.2 - RSA_AES_128_SHA256 environment resulted in total CPU/tx increasing by 2.1% for the SSL server when compared back to a z/VM 6.3 - TLS 1.0 - RSA_AES_256 environment.
A z/VM 6.3 environment
using TLS 1.2, RSA_AES_128_SHA256, and SSL V2.1
experienced a 6.3% increase in CPU/tx in the SSL server
when upgrading to z/VM 6.4.